Hello everyone, I've been working on a hobby project recently, and the first step is to extract as much data from an NDS ROM as possible. In pursuit of that goal I found some information that I couldn't seem to find elsewhere, and I want to share it with anyone interested.
In the GBATEK, part of the ROM header, 0x088, is marked as unknown. Well, here's an official diagram that makes the unknown known!
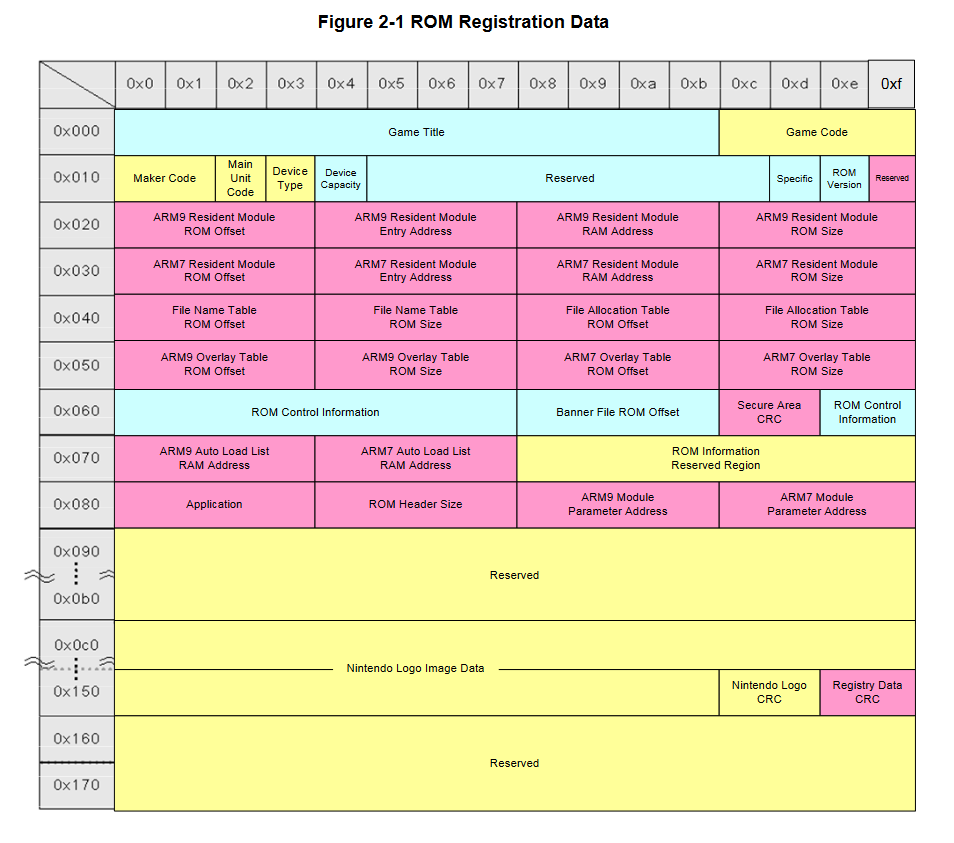
So it turns out 0x088 and 0x08C are the addresses of the ARM9 and ARM7 auto-load parameters respectively. I've got absolutely no idea what this means.
It also occurred to me that a piece of software called the "DS Master Rom Checker" from the SDK is capable of identifying the exact version of the Nitro SDK used to build the ROM, and identify third-party libraries. So I loaded the thing up in a debugger and determined that it searches for a string in the ARM9 binary, "[SDK+", I'd noticed this before but never put two and two together.
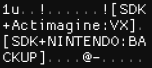
Turns out that it's as simple as parsing the data between "[SDK+" and "]". Split the string at the colon. The left side is the developer and the right side is the library. So it's fair to say that this ROM uses Actimagine's VX video codec somewhere. I have no clue why the Nintendo library is named "BACKUP" but I've seen this in every ROM I've checked so far.
As for determining the version of the Nitro SDK, it is two bytes preceding an array of bytes "21 06 C0 DE DE C0 06 21". The first is the minor version number, and the second is the major version number.
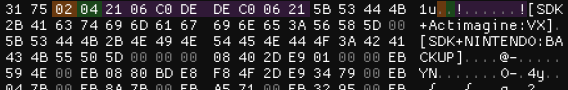
For example, this game was built with version 4.2 of the Nitro SDK. It goes deeper than this as well, you can extract the release type from the two bytes in the very front but I couldn't be bothered to figure out how this worked. What I find odd is that this byte array can be found multiple times throughout some ROMs. It makes me question if this signature was intentional, or if it's some build quirk that made its way into the ROM checker.
Either way this is great information because some versions of the Nitro SDK have been leaked, and it makes me wonder if using something like Ida's FLIRT or Ghidra's FunctionID would be feasible to recover some symbols.
Anyway I hope I've actually posted a new discovery here, and not some common knowledge... I am completely new to the ROM hacking scene.
In the GBATEK, part of the ROM header, 0x088, is marked as unknown. Well, here's an official diagram that makes the unknown known!
So it turns out 0x088 and 0x08C are the addresses of the ARM9 and ARM7 auto-load parameters respectively. I've got absolutely no idea what this means.
It also occurred to me that a piece of software called the "DS Master Rom Checker" from the SDK is capable of identifying the exact version of the Nitro SDK used to build the ROM, and identify third-party libraries. So I loaded the thing up in a debugger and determined that it searches for a string in the ARM9 binary, "[SDK+", I'd noticed this before but never put two and two together.
Turns out that it's as simple as parsing the data between "[SDK+" and "]". Split the string at the colon. The left side is the developer and the right side is the library. So it's fair to say that this ROM uses Actimagine's VX video codec somewhere. I have no clue why the Nintendo library is named "BACKUP" but I've seen this in every ROM I've checked so far.
As for determining the version of the Nitro SDK, it is two bytes preceding an array of bytes "21 06 C0 DE DE C0 06 21". The first is the minor version number, and the second is the major version number.
For example, this game was built with version 4.2 of the Nitro SDK. It goes deeper than this as well, you can extract the release type from the two bytes in the very front but I couldn't be bothered to figure out how this worked. What I find odd is that this byte array can be found multiple times throughout some ROMs. It makes me question if this signature was intentional, or if it's some build quirk that made its way into the ROM checker.
Either way this is great information because some versions of the Nitro SDK have been leaked, and it makes me wonder if using something like Ida's FLIRT or Ghidra's FunctionID would be feasible to recover some symbols.
Anyway I hope I've actually posted a new discovery here, and not some common knowledge... I am completely new to the ROM hacking scene.
